Next-gen code review with AI fixes
Check code quality and resolve vulnerabilities early.
Autofix them in your IDE or via PR.
- 85% less false positives
- Inline commenting in PRs and VS Code
- Automated autofixes
.png)






















Covers all major languages and version control providers

Auto-triage vulnerabilities with AI
Reinventing Traditional SAST Scanning
Traditional SAST scanning falls short
- Lots of false positives: Legacy tools like Snyk or Sonar tend to be very noisy
- No multi-file analysis: Limited context on how you’re using the code.
- No SAST Autofixes: Fixing issues takes lots of work.

Aikido’s SAST scanner: Less false positives and one click fixes.
- High-false positive reduction: Aikido’s SAST scanner reduces false positives by up to 95%
- Multi-file analysis: Track tainted user input from top-level controllers to other files.
- SAST Autofix: Generate SAST issue fixes with AI in just a few clicks.
Your AI code reviewer
Instant feedback, smart detection, and clear PR comments, so you can focus on building.
.png)
Focused, high-signal reviews
Ship safer, cleaner code with AI code review that understands your codebase. Leave hallucinations to the other guys.
Real issues, not “tabs vs spaces”
Built to support real-world engineering, not chase lint errors. Fix bad patterns, complex logic, and hard-to-maintain code with high signal analysis, not pedantic style checks.
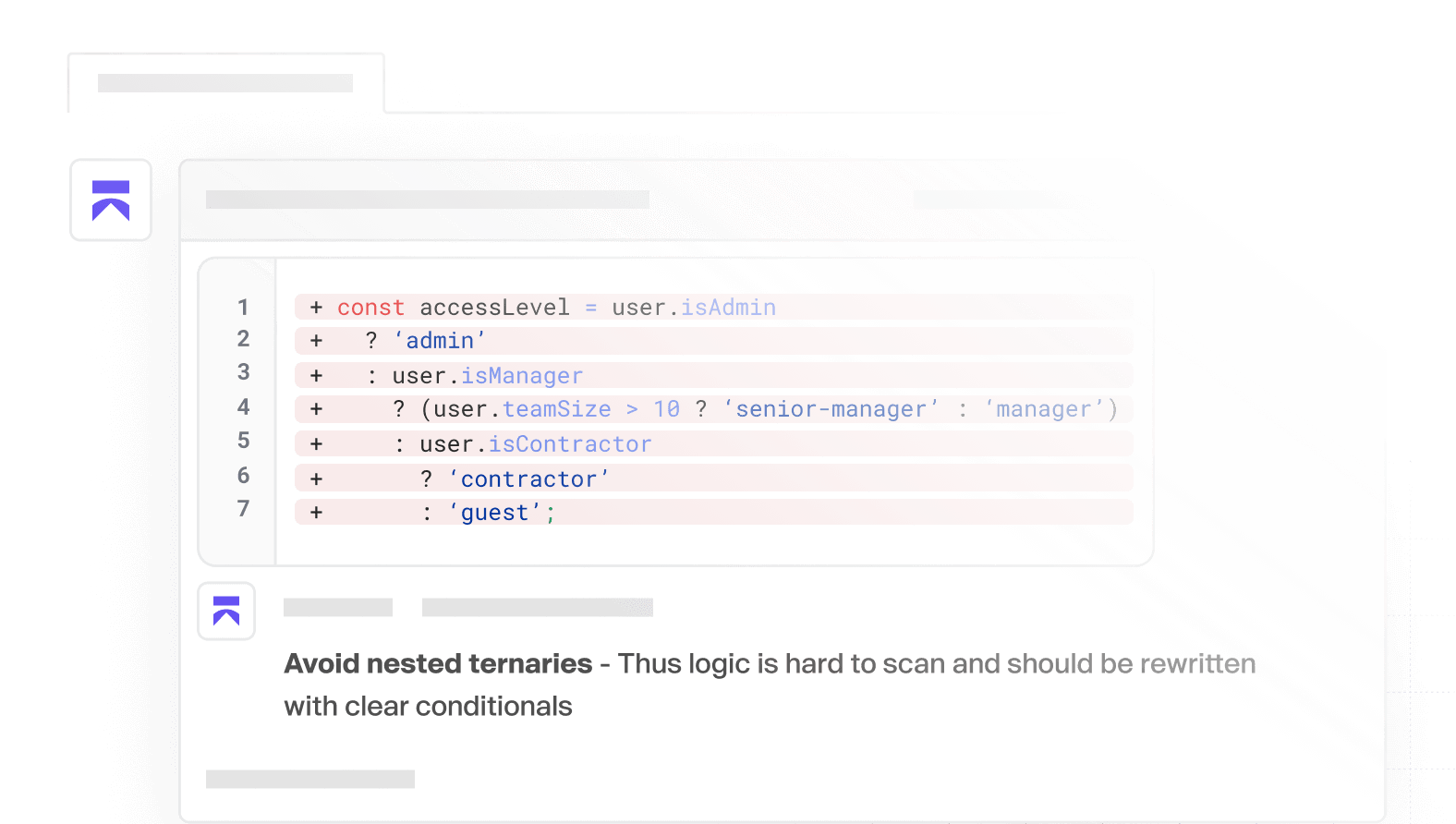
Unreachable return statement
Line after return will never run. Remove dead code.
Magic number in logic
Replace 42 with named constant e.g., MAX_RETRIES for clarity and reuse.
Inefficient array filter inside loop
Avoid filtering inside loop. Cache filtered array or restructure logic.
Early return ignored
A return or conditional is missed by incorrect flow, potentially skipping logic.
Repeated regex compile
Wastes CPU. Hoist regex to module scope.
await inside Promise.all
Inner await serializes work. Remove inner await to parallelize.
Possible Null Reference
user.profile might be undefined. Add optional chaining or guard: if (user?.profile)...
Incorrect Conditional Check
Condition always evaluates to true = due to instead of ==. Use === to avoid accidental assignments.
Division by zero
count can be 0. Add guard: if (count === 0) return 0
Unreachable return statement
Line after return will never run. Remove dead code.
Magic number in logic
Replace 42 with named constant e.g., MAX_RETRIES for clarity and reuse.
Inefficient array filter inside loop
Avoid filtering inside loop. Cache filtered array or restructure logic.
Early return ignored
A return or conditional is missed by incorrect flow, potentially skipping logic.
Repeated regex compile
Wastes CPU. Hoist regex to module scope.
await inside Promise.all
Inner await serializes work. Remove inner await to parallelize.
Possible Null Reference
user.profile might be undefined. Add optional chaining or guard: if (user?.profile)...
Incorrect Conditional Check
Condition always evaluates to true = due to instead of ==. Use === to avoid accidental assignments.
Division by zero
count can be 0. Add guard: if (count === 0) return 0
Smarter, faster PR reviews
Instant PR comments, clear 1-click fixes, and clean summaries in seconds. Cut review time in half. Merge better, faster.


Fast, inline feedback
Get smart, actionable comments directly in your PRs.
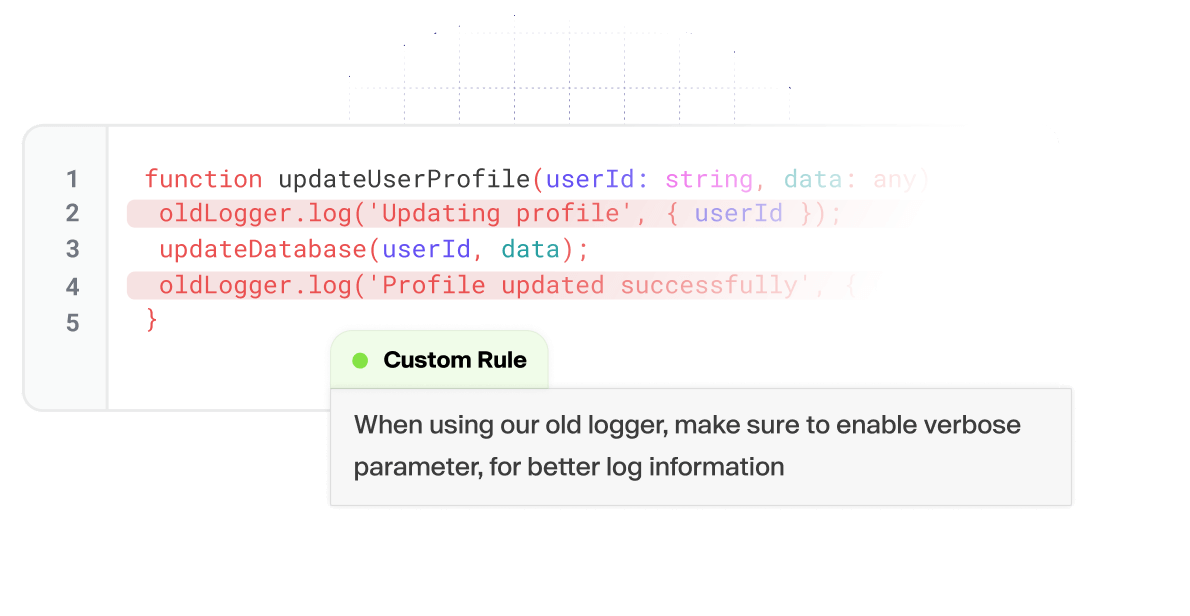
Customizable
Provide codebase context and set custom org-wide rules
1-click fixes
Apply suggested changes instantly, no switching.
.png)
Works out of the box, across your stack
No config. Get smart defaults, full coverage, custom options.
Just connect your repo.


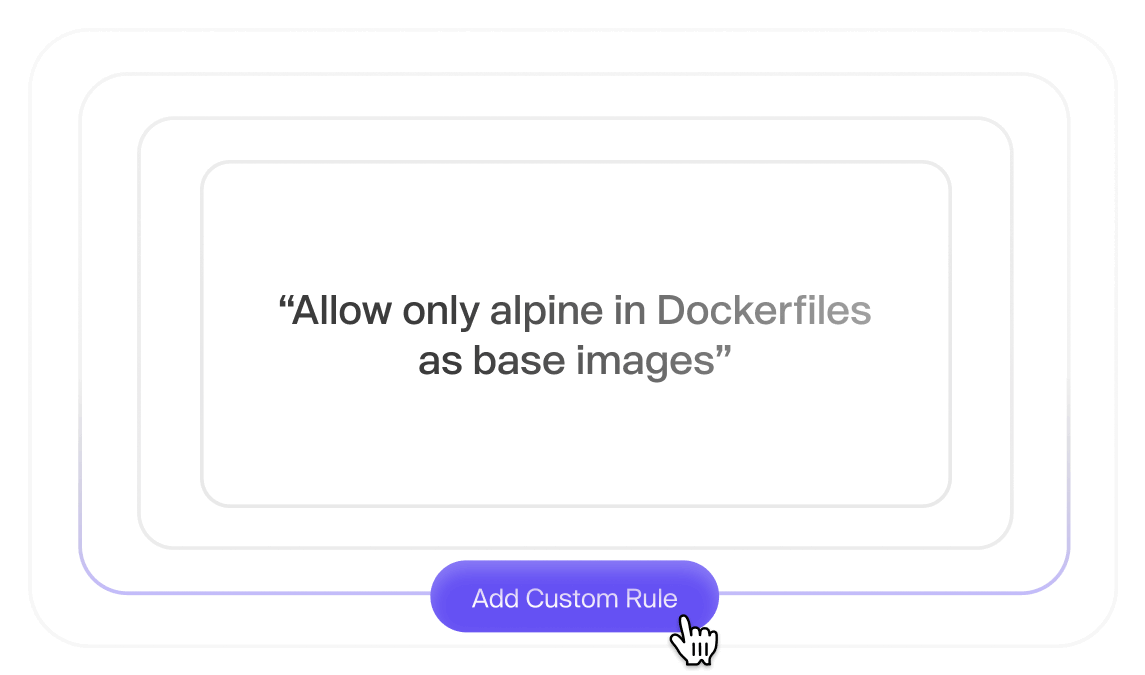
Custom & predefined rules
Enforce rules and style guides on every PR. Pick from the library of pre-defined templates, or write your own.
System & language-agnostic
Review code across multiple languages and systems. Works for your set-up, in seconds.




















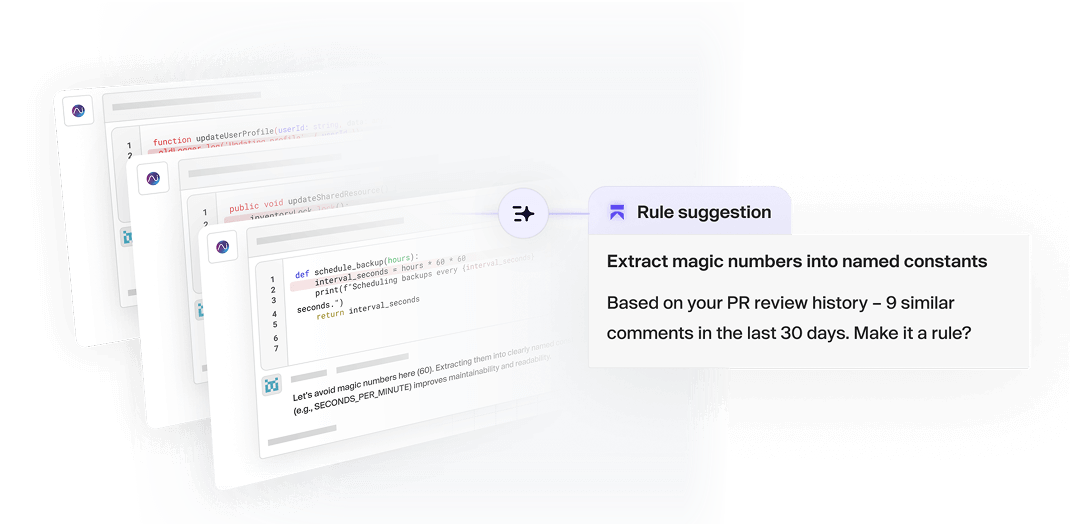
Codebase-aware rule generation
Aikido learns from your team’s past PRs, spotting patterns in review comments and suggesting custom rules based on how your best engineers already work. Turn tribal knowledge into real rules.
Create your own SAST rules
Auto-adjusted severities

Remediation advice
Straightforward remediation advice.
IDE Integration
.avif)
CI/CD Integration

Review your code before it goes to production
Don’t break the dev flow














































































Next-gen code reviews
Improve your team's code quality and security posture in one platform.
.avif)

FAQ
Has Aikido itself been security tested?
Yes — we run yearly third-party pentests and maintain a continuous bug bounty program to catch issues early.
Can I also generate an SBOM?
Yes - you can export a full SBOM in CycloneDX, SPDX, or CSV format with one click. Just open the Licenses & SBOM report to see all your packages and licenses.
What do you do with my source code?
Aikido does not store your code after analysis has taken place. Some of the analysis jobs such as SAST or Secrets Detection require a git clone operation. More detailed information can be found on docs.aikido.dev.
Can I try Aikido without giving access to my own code?
Yes - you can connect a real repo (read-only access), or use our public demo project to explore the platform. All scans are read-only and Aikido never makes changes to your code. Fixes are proposed via pull requests you review and merge.
I don’t want to connect my repository. Can I try it with a test account?
Of course! When you sign up with your git, don’t give access to any repo & select the demo repo instead!
Does Aikido make changes to my codebase?
We can’t & won’t, this is guaranteed by read-only access.


.avif)

















