
TL;DR: The new EU cybersecurity directive, NIS2, is already reshaping how software suppliers do business through stricter vulnerability management requirements in procurement contracts. This shift is gaining momentum, and more companies will need to adapt. Aikido helps automate compliance reporting and vulnerability tracking to meet these new demands. Start your free compliance journey here, or read on to understand what this means for your business.
The Risks of NIS2 Patching Non-Compliance
Picture this: It's 8:33 AM on a Monday. You're triaging your inbox, coffee in hand, mentally preparing for the weekly meeting at 9. Then you see it – the email subject line that makes your stomach drop.
You open the email, you scroll through the usual boilerplate until you find yourself reading – and re-reading – these words:

All software components used for delivering the services must be patched within the following timeframes, depending on the severity of the vulnerability:
- Critical: within 48 hours of the availability of the patch
- High: within one week of the availability of the patch
- Medium: within one month of the availability of the patch
- Low: within three months of the availability of the patch
48 hours for critical vulnerabilities. Not business days. Not "best effort." 48. Hours. Just like that, your Monday turned into a compliance Olympics, and you're competing in every event simultaneously.
These new NIS2 patching requirements aren't just another checkbox – they present a significant operational challenge. Think about it:
- Your team is already stretched thin
- Every new CVE feels like playing security whack-a-mole
- Your deployment windows are tight and getting tighter
- And now you need to document and prove compliance with these aggressive timelines?
Missing these SLAs isn't just about failing an audit: it could mean losing major contracts, facing penalties, or even being cut out of EU markets entirely.
But here's the thing: while other vendors are scrambling to build massive compliance programs and hiring dedicated NIS2 teams, you don't have to.
How to be NIS2 Compliant
We built Aikido specifically for this moment. Our NIS2 compliance is like playing a game on easy mode for these procurement headaches. In literally minutes, you can:
- Generate compliance reports that procurement teams actually accept
- Track your vulnerability SLAs automatically
- Get alerts before you breach any timelines
- Prove your compliance with actual data, not promises
Let's break down exactly what these requirements mean and how you can tackle them without upending your entire 2025 plan.
Sign up for Aikido and get your free NIS2 report in minutes.
What are the Requirements of NIS2?
NIS2 is the EU's latest cybersecurity directive, and it's reshaping how companies handle vulnerability management. EU Member States are transposing NIS2 into national law, often referencing standards like ISO 27001 as a basis for implementation.
Unlike its predecessor, NIS2 covers more industries and imposes stricter requirements – especially around supply chain security. Major enterprises, particularly those in critical sectors, aren't just implementing these requirements internally; they're required to push them down to every vendor in their supply chain.
Read: NIS2: Who is affected?
What does this mean in practice? If you're selling software or services to EU companies, you'll increasingly face procurement requirements that look exactly like the example above. They'll demand specific patch timelines, expect detailed documentation of your vulnerability management process, and require regular compliance reporting. These aren't just checkbox requirements – procurement teams are actively verifying compliance and building these SLAs into contracts.
The most common requirements we're seeing include:
- Defined SLAs for patching vulnerabilities based on severity (the example in the introduction comes from a real procurement doc!)
- Regular vulnerability scanning and reporting
- Documented processes for vulnerability management
- Evidence of compliance through automated tracking
- Regular status updates on remediation efforts
NIS2 Vulnerability Patching Requirements
Let's cut through the legal jargon and focus on what NIS2 actually implies for vulnerability patching. NIS2 itself doesn't prescribe specific patching timeframes. However, it mandates risk management measures, including vulnerability handling and disclosure, which leads to the described SLAs being imposed by software buyers. Here's what procurement teams are looking for:
Response Timeframes
Most enterprises are standardizing on these patch windows:
- Critical vulnerabilities: 48 hours
- High severity: 7 days
- Medium severity: 30 days
- Low severity: 90 days
And yes, these timelines start from when the patch becomes available, not from when you discover it. This means you need to stay on top of vulnerability announcements for every component in your stack.
Documentation Requirements
You'll need to prove three things:
- When you discovered each vulnerability
- When the patch became available
- When you deployed the fix
Without automated tracking, this quickly becomes a full-time job for your security team.
Continuous Monitoring
Gone are the days of quarterly security scans. NIS2 expects:
- Regular vulnerability scanning (most companies interpret this as daily)
- CVEs monitoring for new security advisories
- Active tracking of patch status and SLA compliance
Risk Management
For every vulnerability, you need to:
- Document your severity assessment
- Track remediation progress
- Justify any delays in patching
- Report on compliance with agreed SLAs
This is why we built the NIS2 report in Aikido – it handles all of this automatically. Instead of building spreadsheets and juggling tickets, you get a single dashboard that tracks everything procurement teams want to see.
Implementing with Aikido (Practical Steps)
Here's the thing about compliance frameworks: they're usually a mess of paperwork disconnected from your actual security operations. But it doesn't have to be that way.
Let's say a procurement team asks about your vulnerability management process. Instead of scrambling to create documentation, you simply:
- Connect Aikido to your development pipeline
- Link your cloud infrastructure
- Enable the NIS2 compliance report
- Export the automated evidence of your patching timelines
- Send it off
That's it. No endless documentation sessions. No spreadsheets. No last-minute panics.
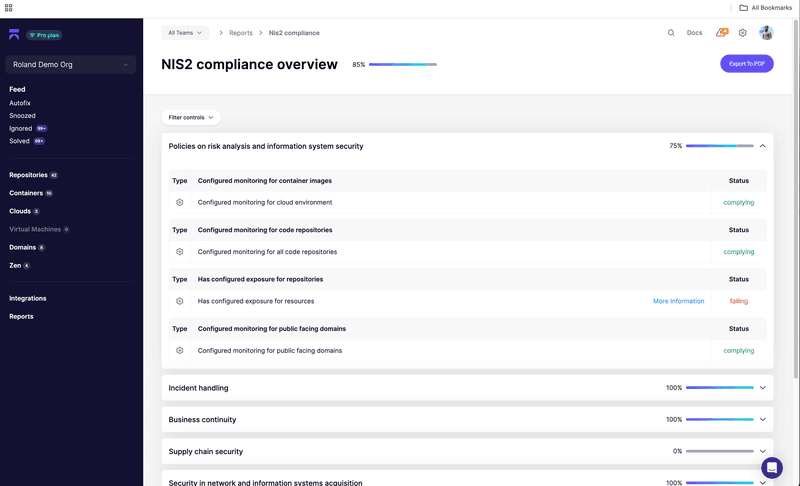
What You Get Immediately
- Continuous scanning across nine risk vectors (from dependencies to runtime security)
- Automated evidence collection for your technical controls
- Real-time compliance status for procurement requirements
- Dynamic reporting that maps directly to NIS2 requirements
The best part? It's working exactly where your developers already are: in CI pipelines, code repositories, and cloud environments. While other teams are manually collecting evidence for their ISO 27001 certifications and NIS2 compliance efforts, you're automatically generating compliance reports from your actual security data.
Next Steps
Let’s wrap up in one sentence: you don't need to build a massive compliance program or hire an army of consultants to answer NIS2 compliance inquiries. We recommend the following strategic approach
- Get a clear picture of where you stand (by signing up for a free Aikido account)
- Run your first NIS2 compliance report
- See exactly what needs attention
- Automate the reporting & easily prove to your customer you're ready for NIS2
While your competitors continue to manage their patch documentation through manual processes, you could have automated compliance reporting up and running in minutes. When future procurement inquiries regarding NIS2 requirements arrive, you can proceed with confidence, knowing your compliance infrastructure is firmly in place.
So the next time you see a procurement email with 'NIS2 requirements' in the subject line? Go ahead and take another sip of that coffee. You've got this one in the bag – or should we say, in the mug.

Secure your software now





.avif)
