Containers have become the backbone of modern DevOps. But they also introduce new security headaches. A single vulnerable base image or misconfigured container can snowball into a major breach across dozens of services.
In fact, recent research found that about 87% of container images carry high-severity or critical vulnerabilities. Add to this the 2026 trends of supply chain attacks and ever-evolving CVEs, and it’s clear that container scanning tools are a must-have. These tools automatically sniff out known bugs, security flaws, and bad configs in your container images (and sometimes live containers) so you’re not shipping ticking time bombs.
We’ll cover the top Container Scanning tools to help your team secure images, workloads, and cloud-native infrastructure before and after deployment.
We’ll start with a comprehensive list of the most trusted platforms, then break down which tools are best for specific use cases like developers, enterprises, startups, Kubernetes environments, and more. Skip to the relevant use case below if you'd like.
- Best 5 Container Scanning Tools for Developers: Aikido Security · Snyk Container
- Best 5 Container Scanning Tools for Enterprise: Aqua Security · Aikido Security
- Best 4 Container Scanning Tools for Startups: Aikido Security · Trivy
- Best 4 Free Container Scanners: Trivy · Grype
- Best 5 Tools for Docker Image Vulnerability Scanning: Aikido Security · Anchore / Grype
- Best 5 Container Security Tools with Runtime Protection: Sysdig Secure · Falco
- Best 5 Container Scanners for Kubernetes Environments: Aikido Security · Sysdig Secure
- Best 4 Open Source Container Scanning Tools: Trivy · Clair
TL;DR
Aikido Security is the container security leader as itdoesn’t just scan images but also secures your whole stack. It’s a developer-centric platform that finds container CVEs, misconfigs, and even suggests base image upgrades via AI AutoFix, all while covering code and cloud as well.
Aikido’s smart deduplication slashes thousands of container findings down to the critical few, and its no-nonsense pricing (free to try, sensible flat plans) means engineering teams get full container protection without budget drama.
What Is Container Scanning?
Container scanning is the process of analyzing container images (and occasionally running containers) for security issues. In plain English, it means scanning the contents of your Docker/OCI images for known vulnerabilities, malware, secrets, or configuration mistakes before those containers run in production.
A container scanner will typically unpack an image, catalog its OS packages, libraries, and configuration, and compare all that against vulnerability databases and security benchmarks.
In a secure DevOps workflow, container scanning is an automated step in the pipeline to flag issues early so developers can fix them as part of normal development, much like compiling code or running tests.
Why You Need Container Scanning Tools
Here are 5 reasons why you need container scanning tools:
- Catch vulnerabilities early: Automatically detect known CVEs and weaknesses in your images before they hit production. This helps you patch or rebuild images proactively rather than reacting to incidents.
- Ensure compliance: Meet security standards and best practices (CIS benchmarks, PCI-DSS, HIPAA, etc.) by verifying your containers don’t contain prohibited packages or configs. Scans produce reports and audit trails to satisfy compliance requirements.
- Integrate into CI/CD: Modern container scanners plug into your CI/CD pipeline or container registry, acting as a checkpoint. They can block risky images from being deployed, all without slowing down development.
- Reduce risk of breaches: By finding critical flaws (e.g. an old OpenSSL library or a leaked secret) and prompting fixes, scanners shrink your attack surface. Fewer known vulnerabilities in containers means attackers have fewer easy targets.
- Automate and save time: Instead of manually checking what’s inside each container, let the tool do the heavy lifting. Teams get consistent, repeatable scans with minimal effort – freeing developers and DevOps to focus on features, not fire-fighting security issues.
How to Choose the Right Container Scanner
Not all container security tools are created equal. When evaluating scanners, consider a few key factors beyond just “does it find vulnerabilities?”. Here are some criteria to keep in mind:
- CI/CD and registry integration: The tool should fit seamlessly into your workflow – e.g. a CLI for pipelines, plugins for Jenkins/GitLab, or registry hooks. If it can automatically scan images on each build or push, you’re more likely to actually use it regularly.
- Accuracy (low false positives): Look for scanners known for high signal-to-noise. The best tools use policy engines or smart filtering to avoid flooding you with irrelevant alerts. Fewer false alarms means developers trust the tool instead of tuning it out.
- Coverage of issues: Consider what each scanner actually checks. Some focus purely on OS package CVEs, while others also flag language library vulnerabilities, secret keys, or config issues. Ideally, choose a scanner that covers the breadth of risks relevant to your stack (images, file systems, Kubernetes configs, etc.).
- Remediation help: Scanning is step one, fixing is step two. Good scanners provide remediation guidance: e.g. “Upgrade this base image to version X to fix 10 vulns” or even 1-click autofix solutions. This can dramatically speed up the patching process.
- Scalability and management: For larger environments, consider if the tool offers a central dashboard or reports, role-based access, and the ability to handle thousands of images continuously. Enterprise teams might prioritize policy enforcement features (like blocking an image that doesn’t meet criteria) and integration with ticketing or SIEM systems.
Keep these criteria in mind as you explore options. Next, let’s look at the top container scanning tools available in 2025 and what each brings to the table. Further down, we’ll dive into the best scanners for specific use cases: from developer laptops to Kubernetes clusters.
Top 13 Container Scanning Tools for 2026
(Listed alphabetically by name; each tool offers unique strengths in securing containers.)
First off, here's a comparison of the top 5 overall container scanning tools based on features like CI/CD integration, remediation support, runtime security, and developer experience.
These tools are best-in-class across a range of needs(from fast-moving dev teams to large-scale enterprise security operations).
Top 5 Overall Container Scanning Tools
1. Aikido

Aikido container scanner makes finding and fixing container vulnerabilities faster, smarter, and far less noisy. It identifies OS package CVEs, library flaws, and misconfigurations, then can auto-generate fixes (for example, suggesting base image upgrades or patch versions) via its AI AutoFix feature.
Now, with Aikido x Root, you can go a step further. AutoFix your containers with secure-by-default, pre-hardened base images. This integration keeps your current base image intact while applying continuous, Root-maintained security patches, shrinking patch timelines from months to minutes and eliminating manual retesting or breakage.
Aikido integrates where developers work, from GitHub and CI pipelines to IDEs, making security checks a seamless part of development. With a modern UI and zero heavy setup, Aikido is as close to “plug and play” container security as it gets.
For organizations looking for a single pane of glass to secure their IT Estate, Aikido’s platform spans SAST, DAST, container image scanning, cloud config scanning, and more, giving you a unified view of security from code to runtime on the cloud.
Key features:
- Reachability Analysis: Zero CVE is not the goal. But making sure you are not exploitable is. Aikido combines 100+ custom rules to reduce false positives and irrelevant alerts with its own reachability analysis engine.
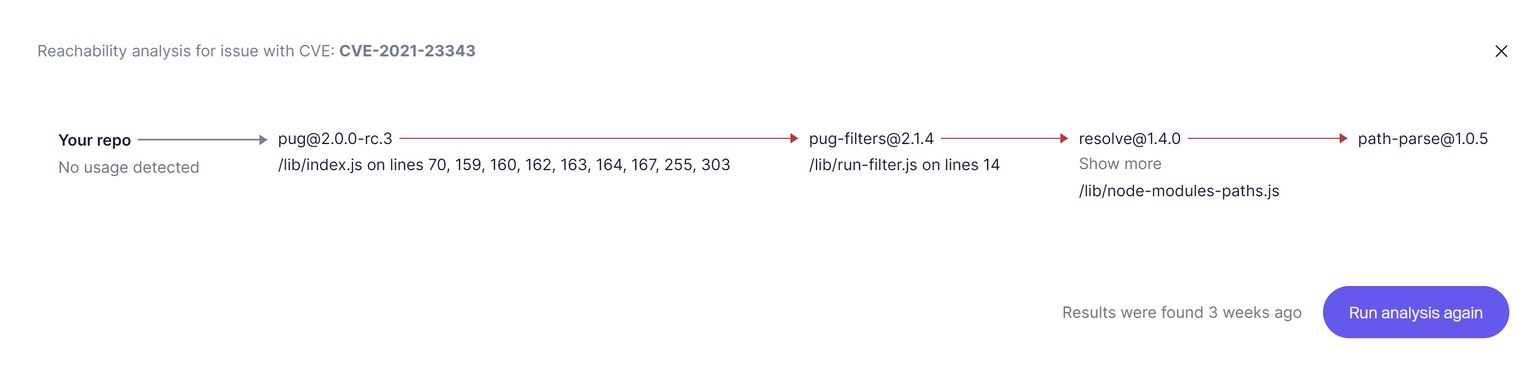
- Aikido’s AI Agent: AI-powered prioritization and one-click AutoFix for container vulnerabilities (cuts remediation from hours to minutes)
- Dev-friendly integrations: CI/CD plugins, Git hooks, and IDE extensions for immediate feedback.
- Secure-by-default images: Through Aikido x Root, AutoFix can now harden your containers automatically with pre-built, continuously patched base images. You keep your stack stable and secure without manual patching or risky upgrades.
- Detects unknown vulnerabilities: Aikido checks the standard vulnerability databases (NVD, GHSA) but goes further using Intel to uncover undisclosed or CVE-less vulnerabilities and malware, providing broader and more proactive coverage.
- Instant Deduplication: Noise reduction through smart deduplication and false-positive filtering (issues are triaged so you only see real problems). Unlike other scanners that will overload you with many separate issues if an affected function is found multiple times.
- End-of-life runtimes protection: Aikido protects your application from outdated, vulnerable runtimes. These often-overlooked components can pose major security risks if left unaddressed.
- Flexible deployment: Cloud service and on-premise options, with compliance reporting (e.g. generate SBOMs and security reports for audits).
Best for:
- Enterprises that want a killer container scanner with AI native features and customizability.
- Development teams and startups that want an automated security tool they can start using in minutes.
- It’s also great for those who don’t have a dedicated security team – Aikido acts like an automated security expert that’s always on.
Aikido is ideal if you want the best vendor for scanning, compliance, and runtime protection across VMs, containers, serverless, and more.
Pros:
- AI-powered AutoFix drastically reduces remediation time
- Low noise through reachability analysis and instant deduplication
- Unified platform covering code, dependencies, containers, and cloud configs
- Seamless developer experience with CI/CD, Git, and IDE integrations
- Detects both known and undisclosed vulnerabilities for broader protection
2. Anchore

Anchore is a well-established container scanning platform known for its policy-driven approach. It provides both an open source engine (Anchore Engine, now succeeded by the CLI tool Grype) and a commercial enterprise product. Anchore analyzes container images for OS and application vulnerabilities and lets you enforce custom policies on your images. For example, you can set rules to fail a build if critical vulnerabilities are present or if disallowed licenses are found.
Anchore’s engine performs layer-by-layer image inspection, mapping each vulnerability to the specific image layer, which helps pinpoint the source (say, a base image vs. an added library). The enterprise version adds a sleek UI, scalability, and integrations with CI tools and registries for continuous scanning.
Key features:
- Robust policy engine: Enforce security gates (e.g. block images with high-severity vulns or outdated packages)
- Detailed SBOM generation:Provides license compliance checks alongside vulnerability scanning
- CI/CD integration: Supports build-time image checks (plugins for Jenkins, etc., or use Anchore in pipelines via Grype CLI)
- Layer-by-layer vulnerability attribution: Making it easier to fix by pinpointing which Dockerfile step introduced the issue
- Flexible deployment:You can use as a hosted service, on-prem, or in a Kubernetes cluster
Best for:
- Teams that need fine-grained control and compliance – e.g. organizations with strict security policies or legal requirements.
- Anchore shines in reducing false positives through policies and ensuring images meet your organization’s security baseline.
Pros:
- Strong SBOM and policy enforcement
- Layer-by-layer vulnerability insights
- Rich integrations with CI/CD and registries
- Supports Kubernetes
Cons:
- Complex setup for smaller teams
- CLI-only experience in open source version
- Can generate noise before policies are tuned
- Slight performance overhead during scans
3. Aqua Security

Aqua Security is a leading enterprise solution providing full lifecycle container and cloud-native security. Aqua’s platform goes beyond image scanning, it covers:
- untime defense,
- Access controls, and
- Compliance
Aqua’s scanner (integrated in its Cloud Native Application Protection Platform) checks container images against a huge vulnerability database (leveraging sources like the NVD and Aqua’s own research). It supports scanning images in registries, on hosts, and within CI pipelines.
Aqua is also known for its tight Kubernetes integration and admission controls: it can prevent pods from running if their images have issues.
In addition, Aqua provides tools like Trivy (open source) for devs and an enterprise console for centralized management.
Key features:
- Comprehensive scanning: Uses one of the industry’s broadest CVE databases for image vulnerability detection
- Kubernetes integration: Automatically scans images in registries or during deployment with built-in policy enforcement
- Runtime protection: Detects anomalous behavior and blocks exploits in running containers through security agents
- Compliance checks: Covers CIS Benchmarks, secret scanning, and configuration validation for regulatory alignment
- Rich reporting: Provides detailed dashboards for risk assessment across large container environments
Best for:
Enterprises needing end-to-end container security.
Pros:
- Comprehensive image and runtime protection
- Deep Kubernetes and registry integration
- Powerful policy enforcement and admission controls
- Robust reporting and compliance features
Cons:
- Enterprise pricing may be high for smaller teams
- Setup and configuration can be complex
- Requires tuning to avoid alert fatigue
- Full feature set only available in paid edition
4. Clair

Clair is an open source container image scanner originally developed by CoreOS (now part of Red Hat). It’s a popular choice for integrating scanning into container registries and CI systems, thanks to its API-driven design.
Clair scans each layer of a container image for known vulnerabilities by matching packages against vulnerability data from sources like Debian, Alpine, Red Hat, etc.
Clair itself is more of a backend service as it stores scan results in a database and exposes an API to query them. Notably, Red Hat’s Quay registry uses Clair under the hood to automatically scan images on push.
As an open source project, Clair requires a bit of setup (containerized services and a database), and you’ll need to wire it into your workflow (or use something like Quay). It doesn’t come with a fancy UI, but it’s a reliable scanner for those willing to tinker.
Key features:
- Layer-by-layer CVE scanning of images, logging vulnerabilities found in each layer (helps understand which layer introduced which CVE)
- Exposes a REST API for integrating scan results into other systems (CI pipelines, registries, etc.)
- Updatable vulnerability database: pulls data from multiple Linux distribution feeds and can be extended for other vuln sources
- Fast, incremental scans – Clair can rescan only layers that changed, rather than the whole image every time
- Fully open source and free to use (Apache license), with a community maintaining CVE feeds and updates
Best for:
- Platform teams and DIY enthusiasts who want a scanner they can integrate deeply into custom workflows or internal platforms.
- Clair is a great fit for deploying in an internal registry or as part of a bespoke CI system. (If you’re using Red Hat-based environments or Quay, Clair may be your default choice for vulnerability scanning.)
Pros:
- Open source and completely free to use
- Lightweight and easy to integrate via API
- Incremental scanning speeds up repeated checks
- Strong community support and frequent vulnerability feed updates
Cons:
- Requires manual setup and database configuration
- Lacks a built-in UI or dashboard
- Limited ecosystem support compared to commercial tools
- No built-in remediation or policy enforcement features
5. Docker Scout
Docker Scout is Docker’s own container analysis tool, built to seamlessly integrate with Docker Hub and Docker CLI. If you’re a developer using Docker Desktop or Hub, Scout adds security insights into your existing workflow. It automatically generates an SBOM (Software Bill of Materials) for your images and flags known vulnerabilities in those components.
One of Docker Scout’s strengths is suggesting remediation paths,for example, it can recommend a base image upgrade that would eliminate a bunch of vulnerabilities. Scout runs as a cloud service with a web dashboard, and also ties into the Docker CLI (you can run docker scout commands to analyze images locally or in CI).
The tool uses continuously updated vulnerability data and even monitors your images over time (alerting you if a new CVE affects an image that was previously clean). Docker Scout has a free tier (for individual devs/small projects) and paid plans for teams.
Key features:
- SBOM generation and analysis: It breaks down your image into layers and packages, listing exactly what’s inside and highlighting vulnerable components
- Vulnerability database matching with real-time updates (powered by Docker’s data feeds, so new CVEs get picked up quickly)
- Recommendations for fixes: suggests newer image tags or package updates to resolve vulnerabilities (with an eye on minimizing image size changes)
- Integrations with Docker ecosystem: view security insights directly on Docker Hub pages or in Docker Desktop, and use CLI commands in CI pipelines
- Policy capabilities to enforce rules (e.g. fail a build if vulnerabilities exceed a threshold, using Docker Scout’s CLI/CI integration)
Best for:
- Developers and small teams already invested in Docker Hub/CLI, who want built-in security checks without adopting a separate platform.
- Docker Scout is a no-brainer if you push images to Docker Hub – it gives you immediate feedback on image risk and how to improve it. (Plus, the basic functionality is free for public repos and one private repo, making it an easy choice for individual projects.)
Pros:
- Seamless integration with Docker Hub, CLI, and Desktop
- Automatic SBOM generation with real-time vulnerability insights
- Actionable remediation suggestions for base images and packages
Cons:
- Limited to Docker ecosystem and Hub-hosted images
- Less customizable than standalone enterprise scanners
- Policy controls are basic compared to specialized tools
6. Falco
Falco is a bit different from others on this list – it’s not an image scanner but an open source runtime threat detection tool for containers. We include it here because container security doesn’t stop at build time, and Falco has become the de facto standard for monitoring container behavior in real time.
Originally created by Sysdig and now a CNCF incubating project, Falco runs on your hosts or clusters and uses kernel-level data (via eBPF or drivers) to watch what containers are doing. It comes with a set of rules that detect suspicious activities like: a container spawning a shell or modifying system binaries, unexpected network connections, reading sensitive files, etc. When Falco’s rules trigger, it can generate alerts or feed into incident response workflows.
While Falco doesn’t tell you about known CVEs in your images, it will tell you if a container is doing something it shouldn’t such as indicating an exploit in action or a misconfiguration.
Key features:
- Monitors running containers (and hosts) at the system call level, catching anomalies in real time (e.g. crypto-mining behavior, file access violations)
- Default ruleset for common threats, plus highly customizable rules (write your own to tailor Falco to your app’s expected behavior)
- Kubernetes audit log integration: Falco can also ingest K8s events to detect things like exec’ing into pods or changes in pod security policies
- Open source and part of CNCF which means an active community and continuous improvement; contributions of new rules for emerging threats
- Lightweight deployment as a daemonset in Kubernetes or system service on any Linux. Alerts can be sent to STDOUT, Slack, or SIEM systems for response.
Best for:
- Teams that need runtime container security to complement image scanning.
- If you want to know when a container starts misbehaving (whether due to a zero-day exploit, insider threat, or just a bad config), Falco is the go-to solution.
- It’s popular in Kubernetes environments where you want an added line of defense beyond admission controls.
Pros:
- Real-time detection of abnormal container and host activity
- Highly customizable rule engine for tailored threat detection
- Lightweight and easy to deploy as a DaemonSet or system service
- Strong community support under the CNCF with frequent rule updates
Cons:
- Does not detect known CVEs or perform image scanning
- Requires tuning to reduce noise and avoid false alerts
- Limited visibility outside Linux-based environments
- No built-in remediation — integrates with external alerting or response tools
7. Grype

Grype is a fast and easy-to-use open source vulnerability scanner for container images and filesystems, created by Anchore. It’s essentially the successor to the older Anchore Engine open source project, distilled into a simple CLI tool.
With Grype, you can point it at a Docker image (by tag or tar file) or even a filesystem directory, and it will enumerate everything inside and find known vulnerabilities. It taps into Anchore’s robust vulnerability feeds for multiple OSes and language ecosystems. One of Grype’s big focuses is accuracy as it tries hard to minimize false positives by using precise matching of package versions. It also supports emerging standards like VEX (Vulnerability Exploitability eXchange) to allow certain vulnerabilities to be marked as not applicable or mitigated.
Grype works well in CI pipelines (it outputs JSON or table results) and pairs with Anchore’s Syft tool (which generates SBOMs). Essentially, Grype gives you a free scanner you can script with minimal fuss.
Key features:
- Scans many image sources: Docker/OCI images (local or remote), directory of files, SBOM files – making it versatile for different use cases
- Supports OS packages and language-specific dependencies (e.g. will find vulnerable gems, npm packages, etc., in images)
- Focus on low false positives and relevant results – Grype’s vulnerability matching is quite smart, reducing noise
- Regularly updated vulnerability database (can work online with Anchore’s feed or offline with downloaded DB)
- Outputs in multiple formats (JSON, CycloneDX SBOM, text summaries) for easy integration into pipelines and other tools
Best for:
- Developers or DevOps engineers looking for a no-frills, reliable scanner to embed in automation.
- If you want an open source tool that you can run in a GitHub Action or a shell script to fail builds on high-severity vulnerabilities, Grype is ideal.
- It’s also great for scanning filesystem contents (not just container images), which can be handy in CI for scanning application dependencies.
Pros:
- Fast and lightweight CLI tool for quick vulnerability scans
- Low false positives with precise package and version matching
- Supports multiple input types including images, directories, and SBOMs
- Easily integrates into CI/CD with JSON and CycloneDX outputs
Cons:
- No UI or centralized dashboard for managing results
- Limited to vulnerability scanning (no runtime or compliance features)
- Requires manual setup for offline database updates
- Output can be verbose without proper filtering or automation
8. OpenSCAP
OpenSCAP is a security auditing tool from the Linux world, and while it’s not exclusively for containers, it can be used to scan container images for compliance and vulnerabilities.
Backed by Red Hat, OpenSCAP implements the SCAP standard (Security Content Automation Protocol) and comes with a library of security profiles (for example, DISA STIGs, PCI-DSS checks, etc.). Using OpenSCAP, you can evaluate an image or a running container host against these profiles to see if it conforms to best practices. For container images specifically, OpenSCAP can scan for known CVEs and also check for configuration hardening (like ensuring certain insecure services aren’t present). It’s often used with Red Hat based containers (there’s even an OpenSCAP container image that can scan other images). The tool is quite powerful for compliance folks but can be overkill if you just want a quick vuln scan.
Key features:
- Compliance scanning: validate containers or hosts against predefined security baselines (CIS benchmarks, government standards, etc.)
- Vulnerability scanning using Red Hat’s CVE data (especially useful for RHEL/UBI container images to find applicable errata)
- Command-line tool (oscap) that can scan container tarballs or even Docker images by ID, producing HTML or XML reports
- Integration with Red Hat tooling (e.g. Red Hat Satellite, foreman, and within OpenShift pipelines for security checks)
- Open source framework, extensible by writing your own XCCDF/OVAL checks if needed
Best for:
- Enterprise security and compliance teams that need to assess container images against strict standards.
- If your org is heavy on audit requirements (say, government or finance sector), OpenSCAP provides a proven way to check containers for both vulns and configuration compliance.
Pros:
- Backed by Red Hat and adheres to industry compliance standards
- Highly customizable through XCCDF and OVAL definitions
- Generates detailed HTML and XML reports for audits and documentation
Cons:
- Steeper learning curve and CLI-heavy workflow
- Limited UI and developer-friendly integrations
- Best suited for Red Hat–based environments
- Overkill for teams needing only quick vulnerability scans
9. Qualys Container Security
Qualys Container Security is part of Qualys’s cloud security suite, bringing their vulnerability management expertise into the container world. Qualys CS provides a centralized cloud service to discover containers and images across your environments (on-prem, cloud, CI pipelines) and scan them for vulnerabilities and misconfigurations.
Qualys uses lightweight container sensors that you deploy on hosts or clusters, which then automatically detect running containers, images, and even orchestrator details.
Vulnerability data is correlated with Qualys’s massive cloud database, and you get a single pane of glass to see all container assets and their security posture. Qualys Container Security can also do compliance checks (like CIS Docker benchmark scanning) and integrates with CI/CD (they offer a Jenkins plugin, for example, to scan images during the build process).
As an enterprise product, it comes with the usual Qualys strengths: robust reporting, alerting, and the ability to handle large scale environments.
Key features:
- Automatic discovery and inventory of containers and images across your infrastructure. You know what images are running where, and their vulnerabilities
- Scanning of images in registries (connects to popular registries to scan new images on push) as well as on hosts
- Container runtime security features: can detect and alert on issues in running container instances (and even block containers that drift from their image baseline)
- Tight integration with DevOps pipelines via API and native plugins (so devs get feedback in their build process)
- Policy-driven enforcement and compliance reporting, using Qualys’s library of controls (e.g. disallow running containers with critical vulns, ensure Docker daemon configs are secure, etc.)
Best for:
- Large enterprises and regulated industries that already use Qualys for vulnerability management and want to extend that visibility to containers.
- If you need unified reporting of VM and container vulns, Qualys is a strong choice.
- It’s also suited for orgs with thousands of containers where automated discovery is as important as scanning (Qualys will help you not miss things running in your environment).
Pros:
- Unified visibility across VMs, hosts, and containers in one dashboard
- Automated discovery of container assets across hybrid environments
- Seamless CI/CD and registry integrations for continuous scanning
Cons:
- Primarily targeted at large enterprises, making it heavy for smaller teams
- Initial setup and deployment can be complex at scale
- Pricing and licensing details are opaque
10. Snyk Container
Snyk Container is a container security product from Snyk, a company that aims to provide developer-friendlysecurity tools. Snyk Container focuses on integrating into the development process. It can scan container images for vulnerabilities in both OS packages and application libraries, leveraging Snyk’s vulnerability database and open source intelligence.
Snyk’s advantage is in context and prioritization: it helps devs prioritize which vulns really matter (for example, highlighting if a vulnerable library in the image is actually used by the application). It also provides guidance on fixes – often suggesting base image upgrades that reduce a lot of vulnerabilities in one go.
Snyk Container plugs into CI/CD (with plugins and CLI) and can monitor images over time (sending alerts when new vulns affect your image). It even can connect to Kubernetes clusters to continuously monitor running workloads for issues.
Key features:
- CI/CD and Git integration: Devs can scan images in their pipelines or even trigger scans from GitHub/GitLab integrations, catching problems before merge
- Developer-focused remediation advice (e.g. “switch to this slimmer base image to eliminate 30 issues”) and the ability to open automated fix PRs for base image updates
- Visibility into Kubernetes: Snyk can connect to a K8s cluster and list all running images and their vulnerabilities, tying into deployment configs (helps bridge dev and ops)
Compliance features like license scanning and config checks, in addition to vulnerability scanning (since it builds on Snyk’s Software Composition Analysis roots)
Best for:
DevOps teams that want to shift security left and make it part of development.
Pros:
- Deep developer integration with Git, CI/CD, and Kubernetes
- Actionable fix advice and automated PRs for base image updates
- Intuitive dashboard for vulnerability tracking and reporting
Cons:
- Paid plans required for advanced features and larger teams
- Known for its high volume of false positives
- Cloud-only service with no on-prem deployment options
- Less suited for highly regulated environments needing full offline scanning
11. Black Duck
Black Duck is a veteran in the application security space, traditionally known for open source license compliance and SCA (Software Composition Analysis). In the container context, Black Duck can scan container images to identify all open source components and their vulnerabilities. It essentially performs deep software composition analysis on your image: extracting the Bill of Materials (all libraries, packages, and OS components) and mapping those to Black Duck’s Knowledge Base of open source risks.
One of Black Duck’s fortes is license compliance – so if you’re concerned about licensing of components in your containers (e.g. avoiding GPL code), it’s very useful. Black Duck’s container scanning often uses a component called “Black Duck Docker Inspector” to analyze images layer by layer. The results feed into the Black Duck Hub (central dashboard) where security and legal teams can see vulnerability info, policy violations, and even perform risk triaging. This tool is usually deployed on-prem or as a managed service, and it’s aimed at large organizations.
Key features:
- Comprehensive BOM analysis: identifies all open source software in the image (down to language libraries) and flags known vulns and licenses
- Layer-specific insight: Shows which layer brought in which components, and thus where a vulnerability was introduced (useful for remediation planning)
- Policy management: you can define policies (e.g. “no components with GPL license” or “no vulnerabilities above medium severity”) and Black Duck will mark images that violate these
- Integration with CI pipelines via Synopsys Detect plugin/CLI, so you can fail builds or get reports during the build process
- Links to detailed remediation info in the Black Duck database, and can file issues or pull requests to update components
Best for:
- Enterprises with a heavy focus on open source governance.
- If tracking licenses and a broad view of component risk is as important as catching CVEs, Black Duck is a strong contender.
It’s used often in industries like automotive, aerospace, or others with strict compliance for software components. Pros:
- Comprehensive SCA and license compliance analysis for containers
- Layer-by-layer insight into component origins and vulnerabilities
- Powerful policy management for security and legal compliance
Cons:
- Complex setup and heavier resource requirements
- Primarily geared toward large enterprises with compliance needs
- Slower scan times compared to lightweight open source scanners
- Enterprise pricing may be high for smaller teams
12. Sysdig Secure
Sysdig Secure is a container security platform that packs both image scanning and runtime security into one product (often termed a CNAPP – Cloud Native App Protection Platform).
With Sysdig Secure, you can scan container images in your CI pipeline or registries for vulnerabilities, and also enforce policies to block deployments that don’t meet your criteria. But Sysdig goes further: using the open source Falco engine, it continuously monitors running containers to detect anomalous behavior. This combination means Sysdig Secure gives you feedback at build time and protection at runtime.
Some standout features include linking scan results to Kubernetes deployments (so you can see which running workloads have vulnerable images), and mapping findings to compliance standards (PCI, NIST, etc.) for reports.
Sysdig also offers a neat capability to suggest fixes, such as telling you which base image version would remediate certain vulns. As a commercial tool, it comes with a web UI, API, and integrations with CI/CD and registry webhooks.
Key features:
- Image scanning + runtime security in one: Vulnerability scans, plus real-time syscall monitoring (via Falco) to catch attacks as they happen
- Kubernetes-aware visibility: Correlates images and containers with Kubernetes metadata (namespaces, deployments), making it easier to prioritize fixes for actively running services
- Policy engine to enforce security during build and deploy (e.g. prevent a pod from starting if it has a blocked vulnerability or if it violates compliance rules)
- Compliance mapping and reporting – out-of-the-box checks for standards like PCI, HIPAA, and custom rules, with evidence from both image scans and runtime data
- Incident response features: Sysdig can record detailed activity (syscall captures) around security events, helping with forensic analysis if a container is compromised
Best for:
It’s particularly well-suited for Kubernetes environments where runtime visibility and image scanning need to go hand-in-hand to truly secure the pipeline.
Pros:
- Unified platform combining image scanning, runtime security, and compliance
- Deep Kubernetes context for prioritizing vulnerabilities in active workloads
- Powered by Falco for real-time threat detection and behavioral monitoring
Cons:
- Enterprise-focused platform with higher pricing than standalone scanners
- Setup and tuning can be complex for smaller teams
- Requires ongoing rule management to avoid alert fatigue
13. Trivy
Trivy (by Aqua Security) has emerged as one of the most popular open source container scanners due to its ease of use and broad coverage. It’s a single binary that requires no complex setup – you can run trivy image myapp:latest and get a list of vulnerabilities in seconds.
Trivy is known for scanning everything but the kitchen sink: not only container images, but also file systems, Git repos, Dockerfiles, Kubernetes manifests, and more. This makes it a handy Swiss Army knife for security scanning in DevOps. It pulls in vulnerability data from many sources (Linux distro advisories, GitHub security advisories for language deps, etc.) and even scans Infrastructure-as-Code configs for issues if you ask it to.
Trivy can output results in tabular form or as JSON (and supports generating SBOMs in SPDX/CycloneDX). It’s also used as the engine for other tools (for example, Harbor registry uses Trivy as a plug-in scanner, and Kubernetes lens tools integrate it).
Being open source, it’s completely free and community-maintained (though Aqua offers a paid version with a UI called Trivy Premium).
Key features:
- Very fast and easy CLI – no prerequisites, up-to-date vulnerability database is downloaded automatically on first run
- Scans multiple target types: container images (local or remote), directories, config files (K8s YAML, Terraform), and even live Kubernetes clusters for workload issues
- High accuracy and coverage, using a wide range of vulnerability sources and fine-tuned parsing (Trivy is praised for finding a lot without many false positives)
- Can generate SBOMs and scan SBOM files for vulnerabilities, supporting modern supply-chain security workflows
- Integrates with CI easily (just add the binary and run it in a pipeline) and has a pluggable output that can feed into tools like Grafana or Slack alerts
Best for:
- Everyone, honestly – from solo developers to enterprises.
- If you need a quick, reliable scan of a container image for known issues, Trivy is often the first tool to reach for.
- It’s free, so it’s great for teams on a budget or those just beginning to add security to their pipelines.
- And even mature organizations use Trivy for specific use cases (e.g. periodic scans of configs or as a backstop to commercial scanners).
Pros:
- Its flexibility to scan more than just images also makes it a valuable general security tool in any DevOps toolkit.
- Fast, lightweight, and easy to run with a single CLI command
- Accurate results with minimal false positives
- Completely free and open source with strong community support
Cons:
- CLI-only interface unless using the paid Trivy Premium UI
- Requires internet access to update vulnerability databases
- Large scans can be slower on the first run due to database downloads
Now that we’ve covered the top tools in general, let’s drill down into the best options for specific scenarios. Depending on whether you’re a developer working on a personal project, a startup CTO, or running thousands of containers in production, the ideal container scanning solution can differ.
Below, we highlight the best container scanners for various use cases, with a quick rationale for each.
Best 5 Container Scanning Tools for Developers
Developers want tools that make security as frictionless as possible. The best container scanners for devs are those that integrate into coding and building workflows without a lot of setup or noise.
Key needs include quick feedback (no one wants a scan that takes 30 minutes), easy CI/CD integration, and actionable results (preferably with fix suggestions) so that fixing vulns feels like part of the normal dev cycle. Also, a bit of developer-centric polish – like an IDE plugin or a friendly CLI – goes a long way.
Here are some top picks tailored for developers:
1. Aikido
Aikido is perfect for developers because it embeds security checks directly into the dev process. You get instant vulnerability alerts in your IDE and pull requests, and its AI AutoFix can even generate patches for you. It’s essentially a developer’s security assistant, handling container scans (and more) in the background so you can focus on coding.
2. Snyk Container
Snyk plugs into GitHub, Jenkins, etc., to scan your images and then opens fix pull requests (like suggesting a higher base image version). Devs appreciate Snyk’s clear reports and the ability to ignore or snooze certain issues via config.
3. Docker Scout
For a lot of developers, Docker is already part of daily life. Docker Scout piggybacks on that, giving you vulnerability insights right in Docker Hub or via the Docker CLI. It’s very easy to use (almost zero learning curve if you know Docker), and it provides quick hints on how to improve image security. This makes it a natural choice for individual devs or small teams who want something simple and integrated.
4. Trivy
Trivy’s super-fast CLI scanning is great for developers who want to run a local check on an image before pushing. It’s as easy as running your tests. Because it also scans config files and source repos, a dev can use Trivy in multiple stages (scan code dependencies, then scan the built image). It’s open source, so you can script and customize it freely – a big plus for devs who like automation.
5. Grype
Grype is another excellent open source developer-friendly scanner, built by Anchore with simplicity and automation in mind. It’s a single CLI tool you can drop into any workflow — just run grype <image> and it lists vulnerabilities clearly and fast. Developers like it because it focuses on accuracy (low false positives) and pairs nicely with Syft, its companion SBOM generator.
If you want an open source, scriptable, no-frills scanner that you can automate or run locally without setup headaches, Grype is a solid pick.
Best 5 Container Scanning Tools for Enterprise
Enterprises typically care about scale, governance, and integration with a broader security stack. The best enterprise container scanning tools offer centralized management, role-based access control, compliance reporting, and the ability to handle thousands of images across various teams and projects.
They should integrate with ticketing systems, CI/CD at enterprise scale, and possibly tie into other security tools (like SIEMs or asset inventories).
Here are top container scanners fitting enterprise needs:
1. Aikido
Aikido Security stands out as one of the few container scanning tools designed with both developer experience and enterprise governance in mind.
From enterprise features like SSO to on-prem deployment (for compliance), and compliance frameworks out of the box, Aikido enables enterprises to not just meet current security requirements, but innovate confidently for the future.
Unlike legacy enterprise tools that often feel heavy and siloed, Aikido focuses on developer-friendly workflows and zero-noise results. That means fewer false positives, faster remediation, and tighter integration with tools enterprises already use.
2. Aqua Security
Aqua is a top choice for big enterprises running containers and Kubernetes. It provides full lifecycle coverage – image scanning, admission control, and runtime defense – with a robust management console. Enterprises value Aqua’s compliance modules (with templates for standards) and its ability to integrate with everything from CI pipelines to cloud accounts.
It’s battle-tested in large deployments, supporting multi-cloud and hybrid environments with ease.
3. Qualys Container Security
Many enterprises already use Qualys for vulnerability management on servers, and Qualys Container Security extends that into the container realm. It’s designed for large-scale visibility, automatically discovering container instances across data centers and cloud. Qualys shines in asset management and compliance: an enterprise security team can get a single pane for “all container images and their vulns company-wide”.
The built-in CI plugins and API also let enterprises blend scanning into complex CI/CD flows. If you need rich reporting and integration with corporate security dashboards, Qualys is a strong contender.
4. Black Duck
Large organizations concerned with open source risk often opt for Black Duck. For enterprise container scanning, Black Duck’s ability to detect every open source component and track license/legal risks is a differentiator. Think of a big enterprise releasing software – they need to ensure no forbidden licenses or unpatched libraries slip through. Black Duck provides that governance layer, with workflows for security and legal approvals. It’s heavy-duty but very powerful for enterprises where compliance and IP risk are top of mind.
5. Sysdig Secure
Sysdig Secure appeals to enterprises looking for a one-stop cloud-native security platform. It’s used by Fortune 500 companies that run huge Kubernetes clusters. The tool’s ability to tie image scanning to runtime context (like “this vulnerable image is running in prod in these clusters”) is invaluable at scale for prioritization.
Enterprises also appreciate features like Sysdig’s integration with LDAP/AD for user management and its advanced analytics (e.g. risk scoring across thousands of images). For a security operations center (SOC) in an enterprise, Sysdig provides both broad oversight and deep drill-downs when needed.
Best 4 Container Scanning Tools for Startups
Startups need security tools that punch above their weight without knocking out their budget. Typically, a startup is looking for something affordable (or free), easy to set up (no time for a dedicated security engineer), and ideally that doesn’t slow down rapid development sprints.
The best container scanners for startups are those that provide strong default security with minimal configuration, and can scale with the company’s growth. Also, flexibility is key – a startup’s tech stack might change quickly, so a tool that covers multiple environments (cloud, on-prem, different languages) is a plus.
Here are great options for young companies:
1. Aikido
For a startup, Aikido offers incredible value: it’s free to start and provides an immediate security blanket over your containers, code, and cloud resources. Also with the Aikido platform that combines many scanners in one, a small team can get SAST, container scanning, and more without managing several tools. It’s like hiring a whole security team in a box.
The fact that it’s cloud-based and up in minutes fits a startup’s need to “just secure it” without fuss. As the startup grows, Aikido can scale and introduce more advanced checks, but on day one it delivers a lot of protection with very low effort – perfect for a fast-moving company.
2. Trivy
Trivy is a fantastic choice for startups because it’s free, open source, and simple. A two-person dev team can use Trivy locally or in their CI pipeline to prevent obvious mistakes (like shipping a critical vulnerability). There’s no procurement process or complex integration – just add the binary and go.
For a cash-strapped startup, Trivy covers the basics of container vulns and even things like IaC scanning, which is a huge win for zero cost.
3. Docker Scout
If your startup’s developers are already fluent in Docker, Docker Scout is an easy win. It provides security insight with essentially no setup (especially if you’re hosting images on Docker Hub). The free tier likely suffices for a small startup’s private repo or two. Scout will make sure you’re not using a blatantly vulnerable base image. It’s a low-effort way to add a layer of security awareness to development.
4. Grype
Another open source gem, Grype is great for startups that want a lightweight scanner integrated into their build process. You can script Grype to run on each pull request or image build; it will fail the build if something egregious is found. Startups appreciate Grype’s simplicity and the fact that it doesn’t require maintaining any servers or paying for subscriptions. It’s a pragmatic tool to enforce a baseline security standard from day one of product development.
Best 4 Free Container Scanning Tools
Looking for container scanning on a $0 budget? There are plenty of high-quality free options – mostly open source tools – that you can use without paying a cent. “Free” might mean different things: some are completely open source and self-hosted, others are SaaS with generous free tiers.
Free scanners are great for individual developers, open source projects, or as a trial run before investing in a paid solution. Keep in mind that while free tools can do the job, you might trade off some convenience (e.g. lacking a UI or enterprise features).
Here are the best free container scanners:
1. Trivy
Trivy tops the list of free scanners. It’s open source, maintained by Aqua Security but free for anyone. You get a broad vulnerability scan (OS packages and app deps) with no setup. The vulnerability database updates are also free, so you’re always scanning against current data. For many users, Trivy alone covers 80% of needs.
2. Grype
Also completely free and open source, Grype is a great alternative (or complement) to Trivy. It focuses on accuracy and integrates nicely with CI. Being CLI-first, it’s perfect for automating scans in a DevOps pipeline at no cost. The Anchore team keeps its vulnerability feeds up-to-date and openly accessible.
3. Clair
Clair is free to use and a good choice if you want a scanning service running in your own environment. While it requires a bit more work to set up, once running, it continually updates its vulnerability data and can be called upon via API to scan images. Using Clair, you can effectively build your own free “container security service” internally. Many smaller registries or self-hosted CI setups leverage Clair for this purpose.
4. Docker Scout (Free tier)
Docker Scout’s basic plan is free, allowing scanning for a limited number of repositories and unlimited public images. This means if you have a small project or are mainly dealing with public open source images, you can use Docker Scout’s cloud service for $0. It’s a nice option if you prefer a web UI and integration into Docker Hub, without deploying anything yourself.
(Honorable mentions in free tools: OpenSCAP – free and open source, though a bit specialized; Dockle – an open source container linter for config issues, useful and free; and CVEbench/CVE-Scanner – various other community tools exist, though Trivy/Grype generally supersede them.)
Best 5 Tools for Docker Image Vulnerability Scanning
If your primary concern is scanning Docker images for vulnerabilities, as opposed to broader container runtime security, there are a set of tools particularly well-suited to that job. “Docker image vulnerability scanning” means taking an image (probably built from a Dockerfile) and identifying known CVEs in it.
The best tools here excel at parsing Linux package managers, language package files, and other contents of the image. They should support Docker/OCI image formats and ideally connect with Docker registries.
Here are the top tools for this use case:
1. Aikido
Aikido’s container image scanning is among the fastest to get results. With a focus on actionable output, it will scan your Docker image and immediately tell you not just what’s wrong, but how to fix it (e.g. “upgrade this package” or even automatically generate a fix PR). For pure vulnerability scanning, Aikido is effective and adds context like risk scores based on whether the image handles sensitive data. It’s a great choice if you want scanning plus the convenience of built-in remediation.
2. Anchore/Grype
Anchore (via the Grype tool or Anchore Enterprise) is purpose-built for Docker image scanning. It parses the image layer contents thoroughly and checks against comprehensive CVE feeds. Anchore’s solutions can be integrated into Docker build pipelines or run on images in registries. They are known for policy-based vulnerability scanning, meaning you can customize which vulns matter. This is excellent when you want fine control over your Docker image standards.
3. Trivy
Trivy again shines as a Docker image scanner. It handles all common base images (Alpine, Debian, CentOS, etc.) and finds vulns in both system packages and application deps inside the image. Running trivy image <image> is a quick way to get a list of CVEs before you push to production. It’s often used by Docker power-users and has very high CVE coverage. If you want a straightforward “tell me what’s insecure in this Docker image” tool, Trivy is hard to beat.
4. Docker Scout
Given it’s by Docker, Scout integrates directly with Docker images and registries. It provides a friendly UI listing an image’s vulnerabilities layer by layer. One unique aspect: it can show you the base image lineage and where vulnerabilities come from, and then recommend a less vulnerable base. For teams heavily using Docker Hub, Scout offers a convenient vulnerability report right on the image page. This makes it ideal for dev teams focused on just improving their Docker image hygiene.
5. Qualys Container Security
For organizations that want to scan Docker images but within a broader security context, Qualys is very strong. It connects to Docker registries (including Docker Hub, ECR, etc.) and scans images as they’re built or updated. The advantage here is the enterprise-grade vulnerability intel Qualys provides – you get rich details on each CVE, impact ratings, and links to patches. It’s possibly an overkill for a small setup, but for a business with lots of Docker images, Qualys ensures no image goes un-scanned and un-tracked.
Best 5 Container Security Tools with Runtime Protection
Container security isn’t just about images at rest, it’s about containers in motion. For runtime protection, you need tools that can monitor containers as they run, detect attacks or anomalies, and sometimes even intervene to stop malicious activity.
Many of the tools in this category combine image scanning with runtime capabilities (because knowing what’s in your image can inform what to watch at runtime).
Key features to look for:
- Behavioral monitoring (like Falco’s approach),
- Firewalling or blocking of suspicious actions,
- Integration with container orchestration tools for quarantine of vulnerable containers, and
- Incident response data capture.
The following are top container security tools that include runtime protection features:
1. Aikido
Aikido’s platform is expanding to cover container runtime protection (it already offers a form of in-app WAF for applications). While primarily known for scanning, Aikido is positioning itself as end-to-end AppSec, which means runtime container/workload protection is on the menu. This could include monitoring for exploits in containers and virtually patching them via its agent or integration. If you’re using Aikido, you’ll likely see runtime protection features (like blocking 0-day exploits) rolling out, making it a promising all-in-one solution for build and runtime.
2. Sysdig Secure
Sysdig Secure (built on Falco’s engine) is a leader in runtime container security. It not only scans images but actively monitors containers’ system calls and network. Sysdig can kill or pause containers when they violate rules, and it provides detailed forensics (capturing system activity around an event). It’s basically like having an intrusion detection system specifically tuned for containers and Kubernetes. For runtime threat defense, Sysdig is top-notch with its real-time detection and response capabilities.
3. Aqua Security
Aqua’s platform includes something called Aqua Enforcers, which are agents on your nodes that do live monitoring and control. Aqua can block suspicious processes, prevent privilege escalations, and even do image integrity checks at runtime (ensuring the container hasn’t been tampered with).
Aqua also supports runtime scanning – checking a running container’s memory for known malware signatures, for example. It’s a comprehensive suite for runtime, often used in high-security environments where containers might be targets of attack.
4. Falco
As mentioned in our top tools, Falco is the open source go-to for runtime security. While it doesn’t block (Falco is detect only; you’d integrate with something else to block), it’s excellent for observing and alerting on bad behavior in containers.
Many teams use Falco alongside other tools (or homegrown scripts to kill containers) to achieve runtime protection. If you want to DIY your runtime security for free, Falco is the core component to use.
5. Qualys (Container Runtime Security)
Qualys Container Security also provides runtime policies. It can, for instance, flag if a running container deviates from the image (like a new process appears that wasn’t in the image’s manifest) – which often signals an injected process by an attacker. It’s more of a monitoring approach, feeding events to the Qualys console.
While not as granular as Falco’s rule language, Qualys focuses on key runtime risk areas (network connections, processes, file changes) and ties it back to your vulnerability data – so you get alerts like “container X with critical vulns is now executing an unusual binary.” This correlation of vuln + exploit behavior is quite useful.
Best 5 Container Scanning Tools for Kubernetes Environments
Kubernetes adds another layer of complexity to container security. In a K8s environment, you not only have images to worry about, but also deployment configurations, cluster settings, and an additional need for automation at scale.
The best container security tools for Kubernetes will integrate with the cluster to scan images in use, evaluate Kubernetes manifests for security issues, and possibly use K8s features (like admission controllers) to enforce policies.
They should also be able to handle the dynamic nature of pods (containers coming and going).
Here are top scanners tailored for K8s:
1. Sysdig Secure
Sysdig is built with Kubernetes in mind. It can map scanned images to the pods and namespaces in which they’re running, giving a clear view of risk in a cluster. Additionally, Sysdig’s admission controller can block pods that violate policies (like running as root or containing a high-sev vulnerability). For runtime, its Falco-based detection is Kubernetes-aware (e.g. it knows pod names, labels, etc., when reporting an issue). If you’re running K8s in production, Sysdig offers a very integrated security solution – from image registry scanning to node monitoring.
2. Anchore
Anchore’s policy engine plays nicely with K8s by preventing the deployment of images that don’t meet your criteria. Using Anchore with something like Kubernetes OPA or via custom controllers, you can create a pipeline where any image that’s to be deployed is checked. Anchore can also scan images already in your cluster via integrations. Its OCI compliance and Kubernetes admission webhook examples make it a good fit if you’re implementing security gates in a cluster.
3. Aqua Security
Aqua has a strong Kubernetes focus. It provides K8s-native controls like a validating webhook that checks images against Aqua’s database at deploy time, netting out any that are disallowed. It also scans your Kubernetes YAML files (either in CI or within the Aqua console) to detect misconfigurations (like overly permissive privileges or lack of resource limits). At runtime, Aqua monitors the cluster for drifts (if a container starts a process that wasn’t in the original image, Aqua can block it). It’s a comprehensive Kubernetes security solution, making it a favorite for companies with large K8s deployments.
4. Falco
For K8s, Falco is often deployed as a DaemonSet to monitor all nodes. It has specific rules for K8s audit events (like detecting if someone exec’s into a pod or if a ConfigMap with sensitive data is created).
Pair Falco with an admission controller (like the Falco-sidekick + OPA combo) and you can actually enforce certain runtime policies too. As an open source, lightweight tool, Falco gives Kubernetes clusters a defense layer with minimal cost. It’s highly recommended to run Falco or similar if you have lots of containers in K8s – it’s like having a security camera in your cluster.
5. Aikido
Aikido can already scan your container images before they reach the cluster (in CI), and it’s working on features to monitor running workloads (e.g. ensuring that no image with critical vulns gets deployed to a live cluster). Aikido’s integration approach – hooking into CI/CD and cloud – means it can be set up to continuously audit your K8s environment for vulnerable images or misconfigurations, with minimal manual effort.
Best 4 Open Source Container Scanning Tools
Open source tools provide transparency and flexibility.You can host them yourself, tweak them, and avoid vendor lock-in. When it comes to container scanning, some of the best solutions are open source. These are great for communities, internal tools, or organizations that prefer open source for cost or philosophical reasons.
Here we highlight the top open source container scanners (some of which we’ve already mentioned above):
1. Trivy
Open source (MIT licensed) and hugely popular, Trivy is often the first recommendation for an OSS scanner. It has an active community, frequent updates, and wide adoption. Whether it’s for a DevSecOps open source project or an internal toolchain, Trivy delivers quality scans without proprietary constraints.
2. Grype
Anchore’s Grype is Apache-licensed and open to community contributions. It’s a solid choice if you want an OSS scanner with corporate support (Anchore backs it but it’s truly open source). The project is actively maintained on GitHub, and many users contribute improvements. Its pairing with Syft (for SBOM generation, also OSS) makes it a nice component in an open source supply chain security stack.
3. Clair
Clair has been around for a while and remains a go-to open source scanning service. Now in version 4 (with support for new distributions and easier setup), Clair is used in projects like Harbor (open source registry) as the default scanner. It’s GPL licensed and community-maintained (mainly by Red Hat engineers). For those wanting an OSS vulnerability scanner service integrated into a registry or CI, Clair is a proven solution.
4. OpenSCAP
OpenSCAP is open source (LGPL), and while it’s more of a compliance tool, it does provide container scanning capabilities as part of the OpenSCAP base. Security-conscious open source users (for example, in Fedora or CentOS communities) use OpenSCAP to verify container images against security guidelines. It’s supported by community contributions and is a staple in Red Hat’s open source ecosystem.
(Also worth noting: other OSS tools include Dockle for config scanning and Tern for SBOM generation – depending on your needs, the open source world likely has a tool or two that fit the bill.)
Conclusion
Securing your containers is no longer optional, it’s a fundamental part of a safe software delivery pipeline. The tools we’ve discussed above help DevOps teams weave security into every stage, from the moment you build an image to the time it’s running in production.
By choosing the right container scanning solution for your needs, you’ll gain confidence that you’re not shipping known vulnerabilities or misconfigurations.
Whether you go with a lightweight open source scanner or a full-featured platform, the key is to integrate it into your DevOps process so it actually prevents issues, not just reports them.
Here’s to safer containers and smoother sailing in your CI/CD!
And if you’re not sure where to start, give Aikido’s a spin. It's an easy way to see immediate insights into your container security and kickstart a more secure DevOps workflow.
To learn more about container security, check out:
- Top Infrastructure as Code (IaC) Scanners – Secure your deployment pipeline end-to-end.
- Top Software Supply Chain Security Tools – Protect everything that ends up in your images.
- Top DevSecOps Tools – See where container scanning fits in your SDLC.



