So, you’re looking for SAST and DAST. Or, you’re looking to understand what SAST and DAST tools are: What are the key differences? How do you use them together? Do you need them?
You’re in the right place. Let’s dive in.
But first, the TL;DR:
- TL;DR: SAST checks your code for vulnerabilities before your app runs, while DAST tests your app while it’s running to find issues that pop up in real time.
- SAST is like an expert dev reviewing your code, DAST is like a hacker trying to break in.
- Using both together helps catch security problems from start to deployment, and ensures your app is safe.
- Shameless plug 😇 - if you’re looking for SAST & DAST, check us out. Get your SAST & DAST covered, so you can get back to building.
SAST & DAST: What you need to know
Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) are two essential methods in application security that help identify vulnerabilities in software.
What is SAST?
SAST, or Static Application Security Testing, is a testing method that analyzes an application's source code in a static or non-running state. It is a “white-box” testing technique.
SAST allows developers to identify vulnerabilities early in the development (SDLC) process, like code development or code review phases. SAST tools are easy to integrate into CI/CD pipelines and IDEs, so you can secure your code as it's written and scan your code before committing changes to the repository.
SAST can detect vulnerabilities like SQL injection, cross-site scripting (XSS), hard-coded credentials, and other OWASP Top 10 vulnerabilities. SAST tools, like Aikido SAST, scan and compare your code to databases of known security vulnerabilities like the National Vulnerability Database (NVD).
Think of it like this, SAST is like having an expert review your code with a fine tooth comb, who gives you immediate feedback on issues they discover.
That being said, SAST is limited and cannot be used to detect runtime or environment specific vulnerabilities, like configuration errors or runtime dependencies. Scanning code requires that you choose a SAST tool that supports your programming language.
Why does SAST matter?
This early detection is crucial as it allows developers to address issues before the application is deployed, making it easier and less costly to fix problems early. SAST is proactive security, it can save a lot of time - and headache - for the future.
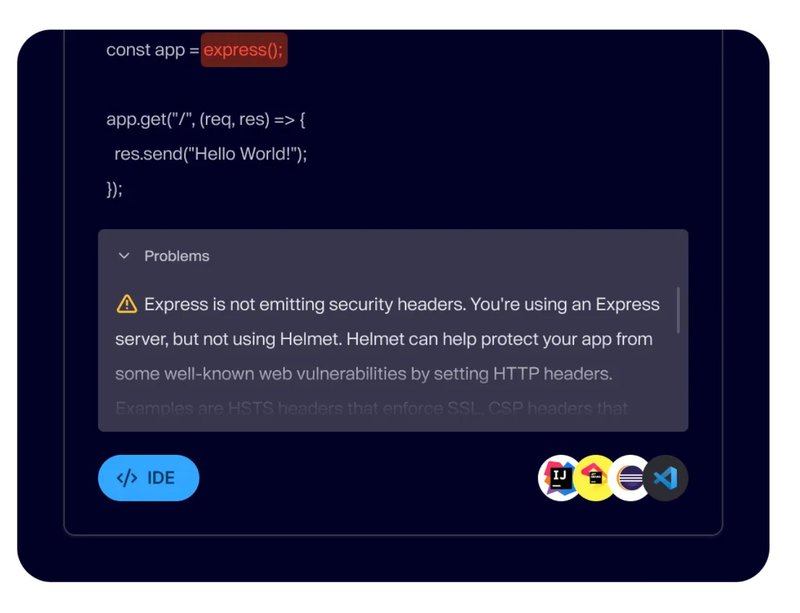
What is DAST?
DAST, or Dynamic Application Security Testing, is a testing method that evaluates an application while it is running.
While SAST sees inside your source code, DAST does not require source code access. Instead, DAST takes an outsider approach to testing your applications security.
DAST simulates attacks on the application much like a hacker would. It is a “black-box” technique.
DAST can also be called “surface monitoring” as it tests the surface or front-end of the web app. DAST tools interact with the application via the user interface, testing various inputs and observing the outputs to identify vulnerabilities such as authentication issues, server misconfigurations, and other runtime vulnerabilities. As DAST works at runtime, that means you need a working application before DAST tests make sense, which is usually around the pre-production and production phase.
Because DAST works externally - and uses standardized protocols like HTTP to connect to your app - DAST is not tied to a specific programming language, unlike SAST.
Why does DAST matter?
This method is important for detecting issues that you cannot detect before deployment. DAST covers you for different categories of errors. DAST identifies risks that come up when the application is up and running, like server or database misconfigurations, authentication and encryption issues that allow unauthorized access, or risks from web services that your application connects to.
Using SAST and DAST Together
Using SAST and DAST together is recommended. Combining SAST and DAST gives you broad coverage across the software development lifecycle. Cover yourself early with SAST and ensure you have real-world resilience later with DAST. This combination allows teams to address vulnerabilities at multiple stages and ultimately leads to more secure applications.
Cheatsheet: SAST vs DAST
Testing Approach:
- SAST: White-box (inside-out) testing. It does not require a running application, working “like an expert developer.”
- DAST: Black-box (outside-in) testing. It requires a running application, testing “like a hacker.”
Access to Code:
- SAST: Requires access to the source code.
- DAST: No access to the source code is required.
When to Use in Software Development Lifecycle (SDLC):
- SAST: Used early in the SDLC. Integrate into your CI/CD and IDE to secure code as it is written.
- DAST: Used later in the SDLC, starting in the pre-production and production phase.
Type of Vulnerabilities Detected:
- SAST: Detects security issues in source code, such as SQL injection, cross-site scripting (XSS), and hard-coded credentials.
- DAST: Detects runtime and environment-related vulnerabilities, such as misconfigurations.
Key Advantages:
- SAST: Identifies vulnerabilities early, allowing for easier remediation that saves time and money.
- DAST: Tests application behavior as a real attacker would, covering a broader attack surface, catching different categories of errors (like configuration issues), and producing low false positives.
Key Limitations:
- SAST: Language and platform-dependent, may produce false positives, and cannot discover runtime or environment-related issues.
- DAST: Cannot pinpoint the exact source of vulnerabilities, requires a running application, and vulnerabilities are more expensive to fix at this stage.
Popular Open Source Tools:
- SAST: Semgrep, Bandit, Gosec.
- DAST: ZAP, Nuclei.

.jpg)

.avif)
